Contents
Creating Amazon Web Services (AWS) Identity & Access Managament (IAM) policies can be time consuming and difficult. You need to know every service that is used, then all the actions, just as a start in creating a least privilege policy. Imagine if you could automatically create a least-privilege policy based on a role you already have? AWS now has that feature!
How it works
Access Analyzer in IAM analyzes your CloudTrail events to get the actions and services that have been used by an IAM user or role. It then generates an IAM policy that is based on that activity. Then you can tune the policy further by adding conditions, and specific resources.
The feature only generates policies with actions for the following common services, any other services you use will just create a policy with the service.
- IAM Access Analyzer
- Amazon CloudWatch
- Amazon Cognito Identity
- Amazon Cognito user pools
- Amazon EC2
- Amazon ECS
- Elastic Load Balancing
- IAM
- AWS KMS
- AWS Lambda
- AWS RAM
- Amazon RDS
- AWS Resource Groups
- Amazon S3
- AWS Security Token Service
- AWS Systems Manager
Limitations and prerequisites
The following limitations and prerequisites are taken from the documentation:
- Enable a CloudTrail trail – You must have a CloudTrail trail enabled for your account to generate a policy based on access activity. When you create a CloudTrail trail, CloudTrail sends events related to your trail to an Amazon S3 bucket that you specify. To learn how create a CloudTrail trail, see Creating a trail for your AWS account in the AWS CloudTrail User Guide.
- Specify a trail in the same account – To generate a policy, you must specify a CloudTrail trail in the same account as the IAM entity (user or role) that you are using to generate the policy. For example, if you have separate development and production accounts, create a CloudTrail trail in both accounts. After you test the policy in your development account, you can later copy the managed policy that you generated into your production account.
- AWS Organizations – You can’t generate a policy using an Organizations CloudTrail trail.
- PassRole – The iam:PassRole action is not tracked by CloudTrail and is not included in generated policies.
- Reduce policy generation time – To generate a policy faster, reduce the date range that you specify during setup for policy generation.
- Use CloudTrail for auditing – Do not use policy generation for auditing purposes; use CloudTrail instead. For more information about using CloudTrail see, Logging IAM and AWS STS API calls with AWS CloudTrail.
- One policy IAM console – You can have one generated policy at a time in the IAM console.
- Generated policy availability IAM console – You can review a generated policy in the IAM console for up to 7 days after it is generated. After 7 days, you must generate a new policy.
- Policy generation quotas – For additional information about IAM Access Analyzer policy generation quotas, see IAM Access Analyzer quotas.
Generate policy
The easiest way to get started is to go to the IAM console, select an existing role, and then expand Generate policy based on CloudTrail events
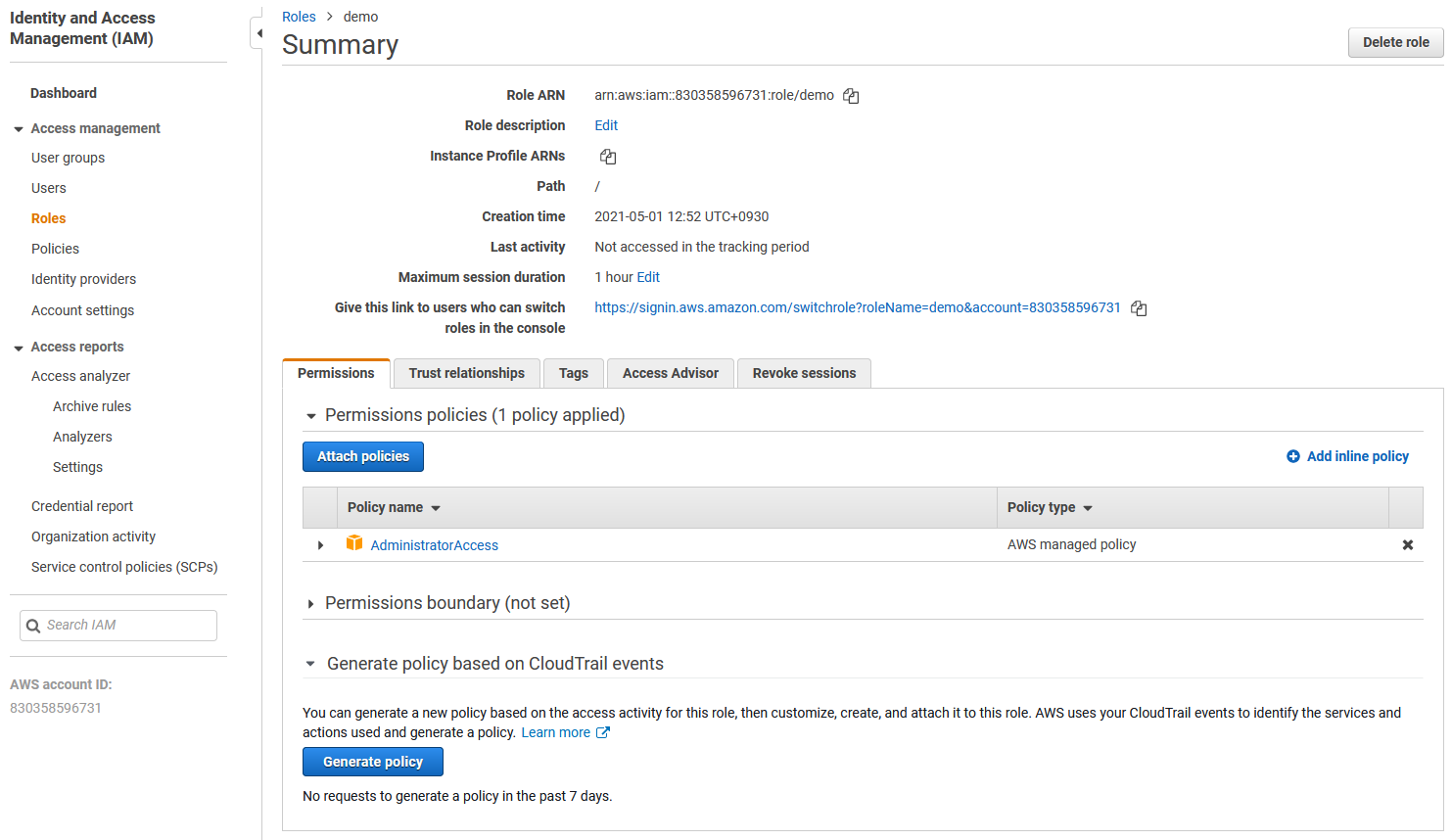
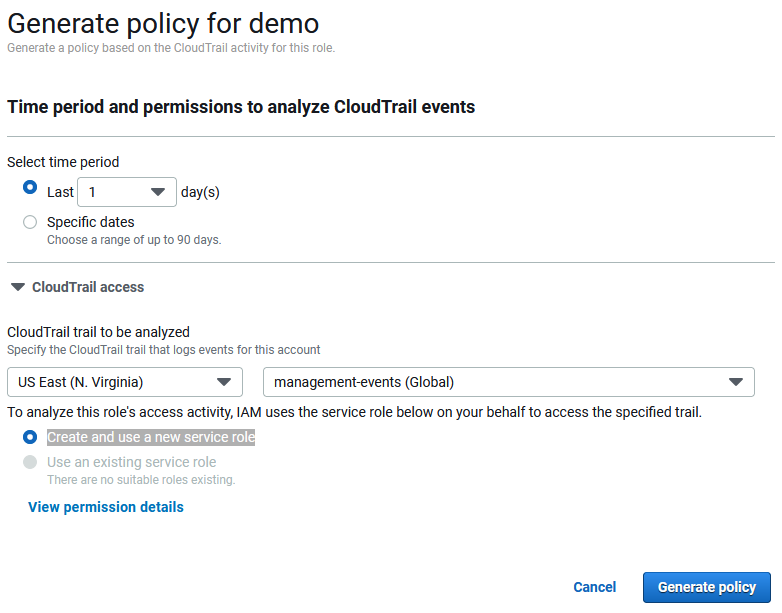
Click Generate Policy then you’ll need to select the time period that it will look at your CloudTrail logs for. The first time you run it you will see an option to Create and use a new service role which you need to do first to give it permission to run. Then click Generate policy.
As long as you’ve met the prerequisites (unlike me as I’m using a trail managed by AWS Organizations) it will run and show Success. Then you can choose View generated policy and see what it cooked up for you! If you want to learn more about following the best practice of least privilege you can see my official AWS blog post on Techniques for writing least privilege IAM policies.
Further reading:
Generate policies based on access activity